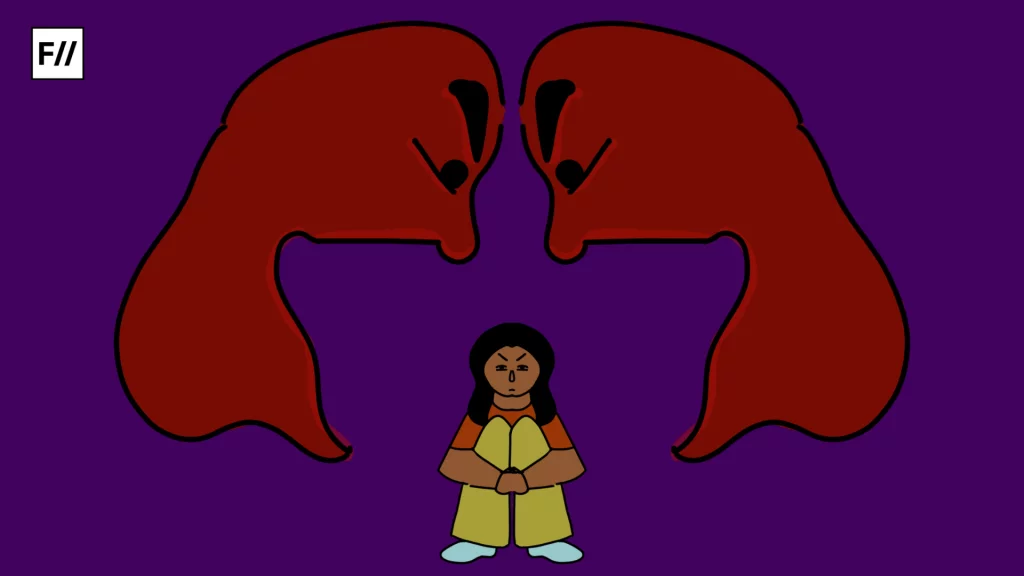
Momentarily, there was safety. Then there was not. While the two preceding statements could possibly be true to the consistent condition of womankind, they ring true for the users of the Tea app. Data breaches, in the 21st-century online world, are frequent and familiar, and most times, the worst victims are women and minorities, whose identities can be weaponised and their safety jeopardised. The latest upturning of cybersecurity has led to the leaking of 70,000 user images, along with government IDs, which definitely included addresses.
The tea overspill: From a safe space to target
The Tea Dating Advice App, a platform exclusively for women to flag potential male partners on a scale of various degrees of harm, was hacked by 4chan users after they had found out its purpose. The app allowed women to post if men were “red or green” flags, were married or potential sex offenders, run reverse image searches to check for fake profiles and gossip with each other. Functioning solely in the US, the app worked as a potent safe space for multiple women – and this information proved to be nefarious to 4chan users, infamous for their virulent and often violent misogyny – who found a compromised database and used it to “doxx” these women. A BBC report revealed that there were two maps with 33,000 pins all across the United States, released to the public.
Many of these were linked to women’s identification documents and selfies that were only meant to be used for “verification purposes”. Disparaging the safety of the lives of these women did not end there, the report stated, “Since the breach, the BBC has found websites, apps and even a ‘game’ featuring the leaked data which encourages harassment towards women who had joined the app. The “game” puts the selfies submitted by women head-to-head, instructing users to click on the one they prefer, with leaderboards of the “top 50” and “bottom 50”. The BBC could not identify the creator of the website.”

Besides this, there emerged another phenomenon: digital methods implemented for the procuring of revenge. This was achieved through multiple channels: copycat apps, websites that compiled all the data leaked from the app, and Telegram channels with some bastardisation of the intent of the Tea app. This time, however, it was for men. Most of these enabled men to write noxious, hurtful stuff about women, letting them “review” them. One such example is the TeaOnHer app, described on the Apple App Store as ‘a platform that requires identity verification, creating an environment for sharing authentic experiences.’
The data breach was celebrated by multiple MRA accounts across social media platforms, with men who had felt like they had been “wronged” coming together to decry “sexism”. Their analysis was simple – that women had set this app up “against” them.
The tea app data breach was celebrated by multiple MRA accounts across social media platforms, with men who had felt like they had been “wronged” coming together to decry “sexism”. Their analysis was simple – that women had set this app up “against” them, and while this app did provide an area for gossip and discussion, like most other apps, they failed to or chose not to recognise the app’s positionality as something similar to a safe space. The breach, therefore, became something that the women should have seen coming – something that they deserved for establishing this sort of male-bereft technocratic femmetopia (which, of course, it was not – an app could barely be even one of those, if not all).
Faith Hill wrote for The Atlantic, “The first breach was awful: humiliating for the women who had to see their images passed around and grim given the number of men making fun of those images with such open, gleeful cruelty. But news of the second breach, which reportedly exposed a larger amount of data with more identifying information, left a pit in my stomach. In more than 1.1 million private messages, women had told one another about rapes, opened up about abortions, and identified cheaters. (“I am his wife,” one user wrote after saying she saw her husband being discussed on the app.) Some shared their phone numbers because, I imagine, they had made connections—because they needed support.”
Data breaches in the femtech world
The big breach in tea app is not the first time that technology catered to women has disappointed its very users by lapses in security. In a study conducted by King’s College London and University College London, researchers found coercive tactics in place with apps extracting sensitive information about fertility from women and then having ambiguous laws regarding the maintenance of privacy of the same. Dr Ruba Abu-Salma told Femtech World, ‘The consequences of leaking sensitive data like this could result in workplace monitoring and discrimination, health insurance discrimination, intimate partner violence, and criminal blackmail.’

The article goes on to state that ‘the study revealed stark contradictions between privacy policy wording and in-app features, as well as flawed user consent mechanisms and covert gathering of sensitive data with “rife” third-party sharing.’ The study revealed that 35 per cent of such apps made claims of not sharing personal data with third parties in their data safety sections but violated it in privacy policies.
A federal American jury found that Meta had illegally accessed data of users on the period-tracking app, Flo. It was also found that Meta had been using the data for ads through an app called App Events, which enables software developers to keep track of user activities and report them back. Krystal Nurse writes for Straight Arrow News, ‘Some of the personal data included answers about whether a person feels pain during sex, sexual activity and relationship status.’ Flo was used to predict ovulation dates and other suggestions for the user’s health.
The big breach in tea app is not the first time that technology catered to women has disappointed its very users by lapses in security. In a study conducted by King’s College London and University College London, researchers found coercive tactics in place with apps extracting sensitive information about fertility from women and then having ambiguous laws regarding the maintenance of privacy of the same.
Flo is not the only app – there are many others. In 2019, Privacy International exposed two other period tracking apps, Maya and MIA Fem, to Facebook. The report revealed that Maya by Plackal Tech (over 5 million downloads on Google Play) is an app that asks for a lot of information and personal data; ‘data about you and your device are relayed to Facebook the moment you open the app, thereby letting them know you are using a menstruation app. Maya informs Facebook when you open the app. There is already a lot of information Facebook can assume from that simple notification: that you are probably a woman, probably menstruating, possibly trying to have (or trying to avoid having) a baby.’
There have been many other apps like tea app – another example could be Evide, which managed data for around 140 charities, including those that work with victims of sexual violence, across Ireland and the UK. Thousands of women found their personal data leaked – along with emails, addresses, and phone numbers. In early 2020, nearly four terabytes of OnlyFans content appeared on platforms like Mega and Google Drive, with the platform denying an official breach. External tech support workers found that the data was almost reprehensibly maintained – and loopholes existed in such a form that they could easily be exploited.
Tea app hack: Tackling data breach risks
Here is the crux of the matter – data breaches are not new. A report by the Indian Computer Emergency Response Team reported 1.32 million incidents between January and October alone in 2023. It also does not require too much analytical thinking to realise that data breaches almost always put women and other gender minorities at risk, more than men. With the almost enormous net that online data spreads out onto the economy of our lives, we venture out into the world knowing that more than half our lives are placed into the hands of people and organisations that we do not know and will never see, just with the hope that the exploitation will not be so visceral that it will affect our lives in a way that it almost feels like violation.

What is necessary is intrinsic structural change with the implementation of stronger, tighter rules around data privacy and access around these apps – not just from corporate organisations, but also from governments. Most of the time, these applications and platforms tend to operate in a vacuum of accountability, where they are safely held by tech exceptionalism and advertising economies that thrive on intimacy turned into metrics. Governments, meanwhile, are slow to churn out meaningful legal and administrative protections and are often quite active in treating women’s digital lives as disposable.
Normality has always been an authoritarian projection — crowdsourced from the richest and most powerful rooms — and this is our new normal, living in the precarity of losing control of all our information, at the brink of not just physical but digital violation — mandated by unchecked companies and uncaring governments, now into forever.
About the author(s)
Saptaparna Samajdar (she/they) is a freelance journalist based in Mumbai. Her interests are primarily music and urban politics.